“How do we get started with security?”
This is a frequent question from clients, but it’s not because they haven’t reviewed the dizzying array of IT security products in the market or considered implementing multifactor authentication (MFA).
Most organizations have rolled out some version of MFA already, along with a checklist to install anti-malware, change passwords frequently, and keeping their system up-to-date.
However, many struggle to move beyond these manual practices toward a modern security practice that can prevent ransomware attacks or quickly recover from data loss.
Without a comprehensive “Zero Trust” strategy to cover the blind spots in your IT security perimeter, your organization’s security plans still fail.
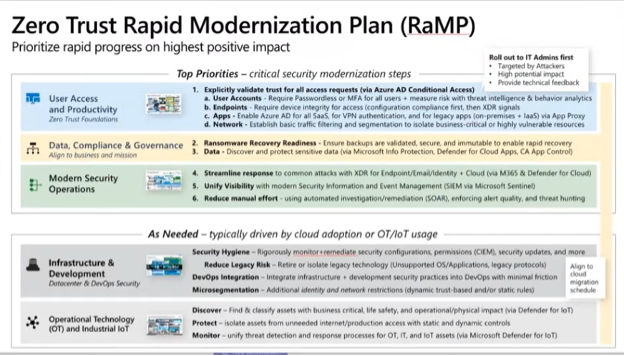
Every organization may be in a different place in their journey to Zero Trust. Engaging with a Microsoft security partner like Finchloom to help guide you — or implement for you —may expedite the process and reduce your risk of a data breach.
1) User Access and Productivity within Zero Trust
The traditional approach to IT security was like a medieval castle, which restricted access (not always successfully), but also flexibility and productivity, as any executive trying to be productive in an airport lounge can attest.
But remote productivity was the promise of the cloud. Internet-based email opened the door to cloud storage for documents, and then cloud-accessible Microsoft Office 365. All accessible with basic security: a username and password.
And as cloud access grew, so did cybercrime: viruses, malware, and now ransomware with data exfiltration and the threat of public exposure.
Network administrators, and developers at Microsoft, struggling to maintain security without sacrificing access or productivity, came up with “Zero Trust” (ZT), an evolving set of IT security strategies that focus on users, assets, and resources instead of the traditional network perimeter-based security policy.
The first step in adopting Zero Trust is to explicitly “validate trust” for ALL access requests through Azure AD, and Microsoft’s new productivity suite, Microsoft 365, which combines Office 365, Enterprise Mobility and Security, Windows 11 Enterprise; and security and compliance tools.
Validating trust for user accounts is much like answering a knock at your door. In the past, we might have said, “Come on in, the door’s open!”
Today, we look through the peephole the validate the one who knocks, to verify the identity and credentials, and to allow conditional access to data and network resources in the following ways:
User Accounts
Identifying the user is the most basic security. Since your username and password can be compromised, Microsoft 365 and Azure AD will require multifactor authentication (MFA), asking for something you know, are, or have:
- Know: a password, key code
- Are: fingerprint scanner, retinal scan, biometric
- Have: a digital code from a fob, token, or security application on your cell phone
The more factors, the stronger your MFA. That is, a password is one factor (something you know), but a fingerprint scan (something you are) is a different factor, making it harder to fake.
Passwordless logins are also available to streamline the validation experience.
Endpoints
Azure AD can improve on standard user validation by also validating based on the endpoint. Is the user logging in from a public library computer or a corporate owned PC? Is this device enrolled in the network already? Is it a public or private network?
Based on the endpoint, your organization can block or limit access to certain resources, or prevent copying and pasting data, or saving to external drives, etc.
Apps
Azure AD can also restrict the interaction between applications, even 3rd party applications. For example, you access Outlook through Microsoft 365 while also pulling up QuickBooks online or a SaaS CRM tool like Salesforce. In traditional security, there’s a potential gap in your session between that validated 365 login and the cloud-based 3rd party software.
But third-party apps can also run through your Azure Active Directory, maintaining a single validated session for all your productivity needs.
Network
Based on user and endpoint validation, your Azure AD can establish virtual networks and VPN tunnels so that users can access specific network resources, and restricting access to open ports or unattended terminal services that are open to the Internet.
Zero Trust Data Compliance and Governance
After verifying trust for your users, endpoints, apps, and your network through Azure AD, your next priority involves the protection of your critical data, both preventing breaches, and planning recovery processes.
Before we discuss specific tools, you should ensure that your organization:
- Schedules and performs regular backups
- Retains backups (read-only; without access to the Internet) for a reasonable duration (based on your organization’s business needs) in case more recent backups are corrupted or infected with ransomware
- Regularly performs restore tests to verify the integrity of the backups
These steps will greatly reduce your risk of having to pay a ransom for your data.
2) Ransomware Recovery Readiness
Staying with the Microsoft suite, we recommend the following two tools for ransomware prevention:
Defender for Endpoint: provides ransomware prevention for your user devices in 7 areas:
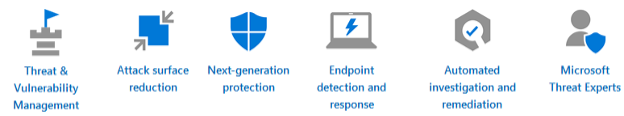
OneDrive Sync with Ransomware Protection: not only compares cloud and desktop versions of your data, but it scans your OneDrive for known ransomware and provides notifications and a wizard for stepping through its removal.
3) Data
As part of the Microsoft 365 suite, the following will help your organization identify and protect your most important data.
Microsoft Information Protection (MIP): encrypts your business-critical data to provide a first line of defense against malicious actors attempting to look at your private data.
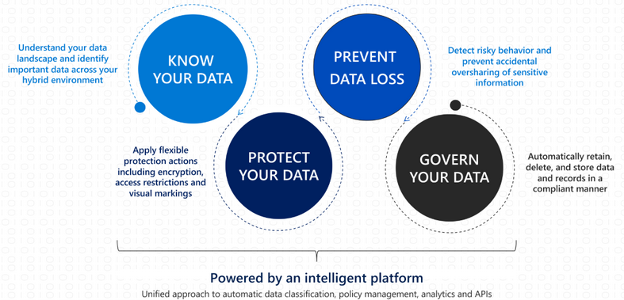
Defender for Cloud Apps: as a Cloud Access Security Broker (CASB), it provides granular visibility into and control over your sensitive data, your user’s activities, and the cloud resources they use, in real time. For example, it will prevent remote employees from downloading contracts to a personal Dropbox.
Defender for Cloud Apps (along with Azure AD) also includes Conditional Access App Control (CAAC): that can block certain applications from running during a user session. For example, instead of preventing a Dropbox download, you can disable Dropbox while other applications are open.
Modern Security Operations
Once you’ve established a baseline for validating trust, and protecting your data, your next priority is to modernize your IT security practice, allowing automated workflows to improve your day-to-day productivity.
4) Streamline Response
Once Microsoft 365 Defender tools begin processing alerts and notifications, you will need a team to review, prioritize, assign, investigate, remediate problems. Otherwise, the tools are as useful as no IT defense at all.
And, as we’ve seen, tech alerts become a white noise that may be ignored if effective tools are not implemented to help this process.
5) Unify Visibility
Instead of having multiple dashboards covering various elements of your infrastructure, Microsoft Sentinel (formerly Azure Sentinel) provides an integrated SIEM tool (Security Information and Event Management) to present all available inputs in one view. That is, it aggregates and flags anomalous activity so that IT team members can investigate.
The consolidation of a variety of security tools into Microsoft 365 and Azure AD makes implementation even easier.
6) Reduce Manual Effort
Microsoft Sentinel’s other integration is SOAR (Security, Orchestration, Automation, and Response) to provide incident response, investigation, and case management tools and workflows to manage potential threats. SOAR is able to compare alerts against existing threat databases and automatically respond, or recommend remediation steps to team members.
If you have ever received an alert saying that your email detected a malicious threat and already moved the email to quarantine, you have experienced a type of SOAR in action.
The key to Sentinel’s success may be how it’s SIEM + SOAR work together to identify an hunt threats, remediating potential problems before they become real problems.
Zero Trust, In Summary
As you can see, implementing Zero Trust practices is no easy feat. If your organization has specific questions about any of the products or services mentioned in this blog, please feel free to reach out by filling out the form here. Similarly, you can view the on-demand webinar we have on this topic by visiting this page, or sign-up for our open service hours here.


