Multi-Factor Authentication (MFA)
Help protect your organization against breaches due to lost or stolen credentials with strong authentication. Secure any app with just one step. Implement MFAWhat is Multifactor Authentication?
Multifactor authentication (MFA) adds a layer of protection to the sign-in process. When accessing accounts or apps, users provide additional identity verification, such as scanning a fingerprint or entering a code received by phone.
Why you need MFA
Its more secure than passwords
- In most identity attacks, it doesn’t matter how long or complex your passwords are
Some types of multifactor authentication are stronger than others
- Make sure your credentials for high-risk accounts are resistant to phishing and channel jacking
Passwords are making you vulnerable
- Protect your business from common identity attacks with one simple action

Multifactor Authentication
Powered by Azure AD
Azure AD offers a broad range of flexible multifactor authentication (MFA) methods—such as texts, calls, biometrics, and one-time passcodes—to meet the unique needs of your organization and help keep your users protected.
Choose the right technology
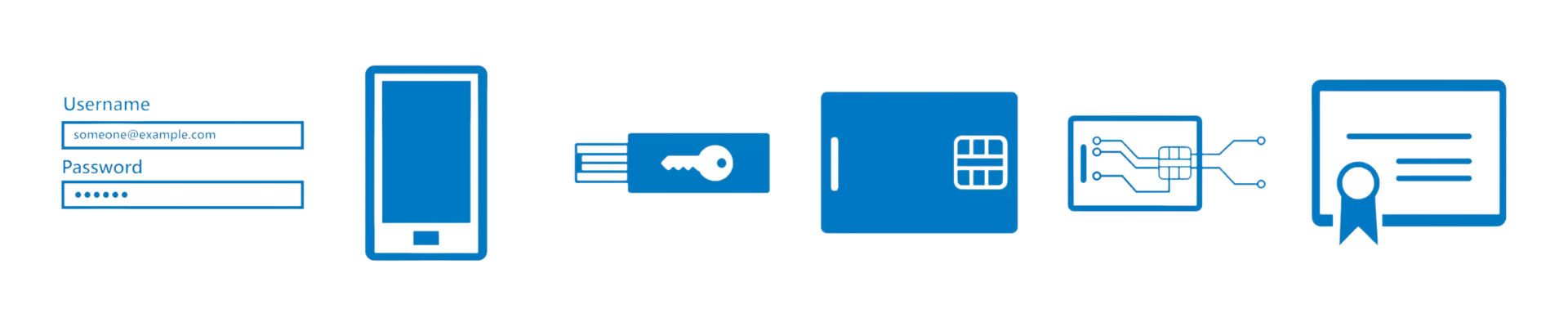
Azure AD multifactor authentication (MFA) works by requiring two or more verification methods.
- Microsoft Authenticator
- Windows Hello for Business
- FIDO2 Security Keys
- Hardware Tokens
- Software Tokens
- SMS and Voice
Approve sign-ins from a mobile app using push notifications, biometrics, or one-time passcodes. Augment or replace passwords with two-step verification and boost the security of your accounts from your mobile device.
Replace your passwords with strong two-factor authentication (2FA) on Windows 10 devices. Use a credential tied to your device along with a PIN, a fingerprint, or facial recognition to protect your accounts.
Sign in without a username or password using an external USB, near-field communication (NFC), or other external security key that supports Fast Identity Online (FIDO) standards in place of a password.
Automatically generate a one-time password (OTP) based on open authentication (OATH) standards from a physical device.
Use the Microsoft Authenticator app or other apps to generate an OATH verification code as a second form of authentication.
Receive a code on your mobile phone via SMS or voice call to augment your password security.

When to Implement MFA
Businesses generally have some sort of access management policies already in place, and MFA is no different. Getting started with one time codes via SMS and voice is an easy way to get right into MFA utilization and further develop security policies.
Once users are all onboarded onto one version of MFA, those with multiple company devices (ie a computer and phone or tablet) can then be upgraded to Microsoft Authenticator or Windows Hello for Business.
MFA options are included in all Azure AD subscriptions.
Interested in learning more about Conditional Access?
How to start with MFA through Azure AD
To get started with MFA, many companies opt to utilize this tutorial provided by Microsoft. If you are already using some sort of MFA policy and want to expand your utilization, a partner like Finchloom can analyze your environment as it currently operates and make specific recommendations to your business regarding implementation.
