Active Directory revolutionized the LAN (Local Area Network) around the year 2000 when it started to take over the business directory business from Novell Networks. I know this because I lived it. It was one of my first projects for Dole Food Company to upgrade from Novell to Active Directory. Active Directory was great! I got certified. I learned how to migrate to it from Windows NT workgroups. I became a Domain AND an Enterprise Admin!
It was a place to put usernames, passwords, security groups, and computer objects. I could apply settings and really gain organization and control over user access and devices. Also, as a side note – that’s around the time Systems Management Server (SMS) started to gain traction giving curious admins like me a way to get inventory, remote control of Windows NT Workstations, and an ability to push out applications to the users. Those were the days.
The problem though is that it’s now 20 years later and many companies still rely on an old Active Directory that is almost always broken in some way.
EVERY SINGLE CLIENT I’VE EVER WORKED WITH IN THE PAST 15 YEARS HAS A MESSED UP ON-PREM ACTIVE DIRECTORY!
Well, I kinda like saying that like a clickbait headline just to prove a point. But really, most every Active Directory environment I’ve seen have some issue or another. Sometimes, it’s because the company has endured multiple administrators who have each made their mark on the Active Directory over time – some documented, some not. Some best practices, most not. Or, maybe a company just has ancient business software that is holding them back and relies on a certain OU structure. Sure, Windows Server and Active Directory may have served you well for many years and “did what it needed to do” and “what’s not broken, don’t fix”, etc…
…But then the cloud came along, and everything changed. Along with the cloud revolution, huge security breaches started taking place. It no longer became feasible to buy your own server, put it in your storage closet, and host your own applications. You can’t just use passwords and a firewall and call it a day anymore (Well, you really never could – but some thought so). Users don’t access apps and data from just inside the friendly confines. They are mobile and more connected than ever!
You simply can’t keep doing things the same way with an old Active Directory running on-premise. I mean, you don’t put your money in a box under your desk, right? You put it in a bank. The banks can build a bigger better safe and better security to protect your money. Just like cloud brings about bigger and better opportunities for your business technology – with bigger and better Datacenters around the world, and the best set of security tools around Cloud.
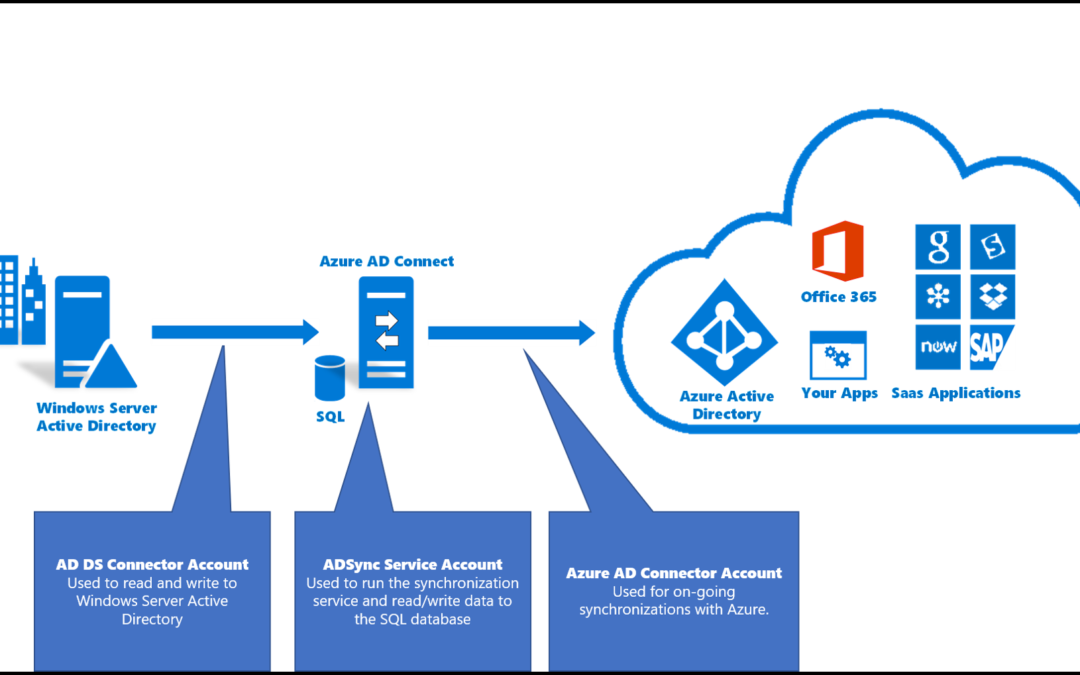
The two things you should start with are Microsoft Azure Active Directory (Azure AD) and Microsoft Intune. Azure AD gives you the modern identity platform to store your users and devices and control access and policies. It’s like other identity products Okta, or OneLogin, or Duo. And you can setup a hybrid Active Directory connecting your On-Prem Active Directory to Azure AD for the time being to ensure a smooth start to your migration and then eventually cut it off and get rid of your Domain Controllers!


When combined with Microsoft Intune, you get the full MDM and Application Protection policies to control business data across all devices (PC, Mac, iOS, and Android) and mobile apps. Intune exceeds many expectations from customers who use Mobile Iron, or AirWatch and find the integration with Azure AD to be a huge benefit. By using Conditional Access with Azure AD and Intune, you can prevent legacy mail clients from connecting (ActiveSync), you can dictate which devices can access your organization data, and you can enforce levels of verification to prove who the user is to avoid impersonation.
And this brings me back to Active Directory and how I want to rid the world of it.
EVERY SINGLE CLIENT I’VE EVER WORKED WITH IN THE PAST 15 YEARS HAS A MESSED UP ON-PREM ACTIVE DIRECTORY!
Group Policy Objects are a mess and usually don’t work right. Multiple upgrades and migrations have taken place across many domain controllers and servers. Tons of disabled users or even enabled users that have rights you didn’t remember giving them still exist in the directory. You’re still using logon scripts. Active Directory replication isn’t working well. You have a root domain and a child domain when you didn’t really need it. I could go on and on and on. Bad Active Directory is a blocker or prohibitor of almost all technology projects and it needs to go.
When I sat in front of a large customer 3 years ago and boldly proclaimed that they should start planning to retire their Domain Controllers, they looked at me like I was crazy. But it really is a reality now that you can start your move of your Users, Passwords, Groups, and all the other things like Multi Factor Authentication (MFA), Conditional Access, Single Sign On (SSO), Mobile Device Management (MDM) by using Azure AD and Intune.
Once the user’s identities are in the cloud, customers can extend Single Sign On (SSO) to other 3rd party cloud apps (like Salesforce, Workday, ServiceNow, and 4000 others). Also, if they have legacy apps that are holding them back, we can show them how we can modernize their apps by moving them to Azure.
Companies of all sizes can protect against 90%+ of all attacks by implementing Multi Factor Authentication and stop relying solely on passwords that you force your users to change every 90 days. Not only does an employee need a password to get in, they also must prove who they are one other way – through a text code, an authenticator app, or a phone call. This is the absolute easiest thing you can do right now to protect your business. It’s easy and users will learn to have their phone ready when they login.
IT Admins – start protecting the devices, locations, and clients your employees use to access your company apps and data. If you use Microsoft 365 for Email, Files, and Teams – you know that you don’t want employees connecting from a public computer or downloading data to unknown and potentially infected shared computers. With Azure AD Conditional Access, you can now dictate what types of devices can access your company data and you can apply rules to that data so that people can’t download it or share it.
Microsoft is giving us free money to do workshops with customers. Help us spend Microsoft’s money and let’s do a workshop to show you how to get rid of Active Directory and modernize with Azure AD.