In the past, we wrote a blog and hosted a webinar on the topic of Defender for Endpoint P1. P1, a great tool for business, is only a partial plan and missing some features that businesses with larger IT departments may utilize. In this blog, we will cover the topic of Defender for Endpoint P2. If you are interested in learning more about Defender P1, please read our blogs on Defender for Endpoint and Defender for Business or watch the webinar using this link. To register for our Webinar for Defender P2 on March 10th at 11AM PST, please click here!
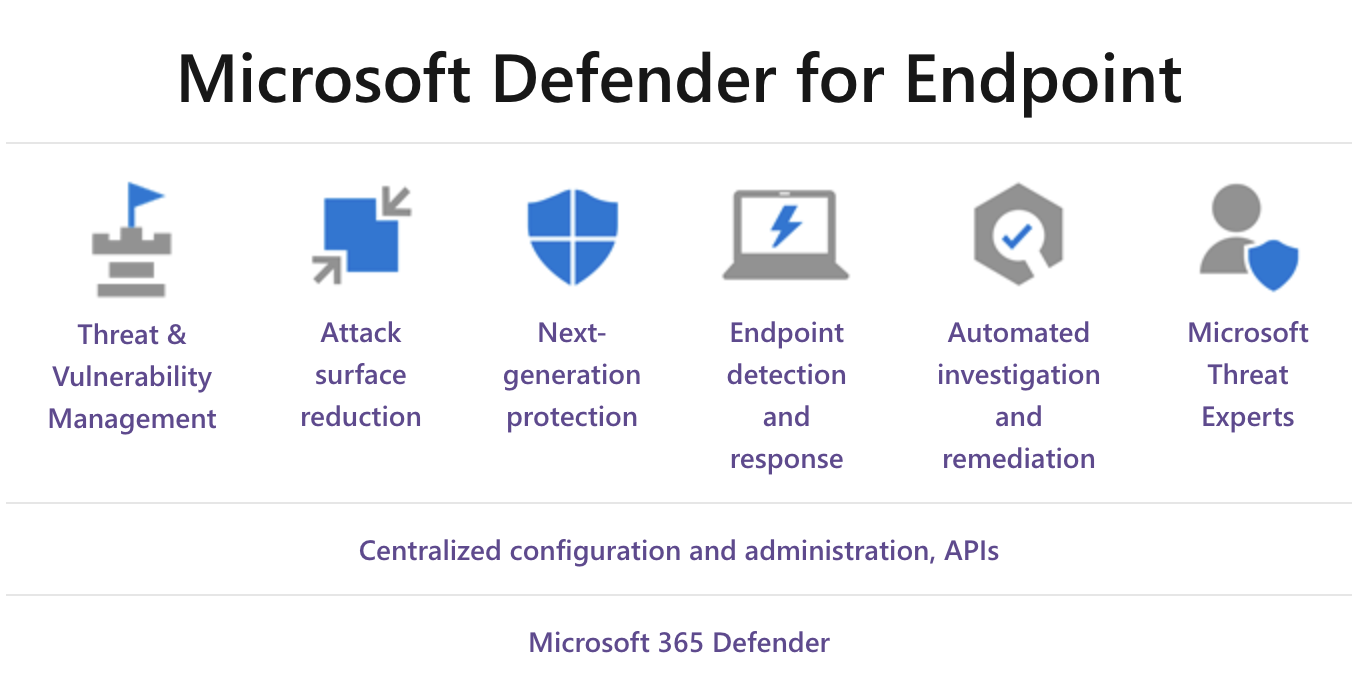
Defender for Endpoint P2 is broken down into 8 basic pieces, each of which are elaborated upon below. Defender for Endpoint P2 includes all the features of P1:
- Attack Surface Reduction
- Next-Generation Protection
- Centralized Configuration and Administration, API’s
And additional features including:
- Threat and Vulnerability Management
- Endpoint Detection and Response
- Automated Investigation and Remediation
- Access to Microsoft Threat Experts
- Microsoft 365 Defender
Attack Surface Reduction
Utilize Windows Firewall and some of the other features of Windows 10 and 11 Enterprise to inhibit access and shut down select features. For example, Attack Surface Reduction can prevent access to the BIOS or provide the ability to turn off USB storage. This is the first line of defense in Defender. By ensuring that configuration settings are set properly, and exploit mitigation techniques are correctly utilized, it is easier to resist attacks and exploitation attempts. Attack Surface Reduction also includes network and web protection to regulate access to malicious IP addresses, domains, and URLs.
Next-Generation Protection
New threats face businesses daily, and companies that are only looking for known threat types are at a disadvantage to malicious actors and software. Defender for Endpoint uses next-generation protection designed to catch all types of emerging threats that can compromise your business.
Threat and Vulnerability Management
Built into the P2 plan is a game-changing risk-based approach to the discovery, prioritization, and remediation of endpoint vulnerabilities and misconfigurations. By looking at real-time threats and risks through inventorying software, Defender P2 provides recommendations for remediation and enables you to set up remediation activities or manually fix the issues. All endpoint data is funneled through, and then visualized on an easy-to-read dashboard with the suggested remediation steps.
Centralized Configuration and Administration, API’s
Integrate other tools using APIs that are native to the apps you are using. The Defender for Endpoint client works across all platforms, and can be installed on Windows 10 and 11, Windows Server, Mac OS, Android, and iOS.
Endpoint Detection and Response
Endpoint detection and response capabilities are put in place to detect, investigate, and respond to advanced threats that may have made it past the first two security pillars. In layman’s terms, endpoint detection and response (EDR) can be thought of like looking for a needle in a haystack. Utilizing the ‘Assume breach’ mindset, Defender for Endpoint continually collects and analyzes activity. Most of the activity that is being analyzed is going to be safe and normal user activity, but sometimes the system or threat hunters (people who look through this data) start to detect certain patterns. Utilizing EDR, you can look for things beyond the typical antivirus and/or anti-malware, and look for hidden hackers, rootkits, or something on a machine that allows malicious actors to connect to it remotely and that may not be detected by traditional antivirus. Advanced hunting also provides a query-based threat-hunting tool that lets you proactively find breaches and create custom detections.
Once a threat is detected, organizations need to respond in a variety of ways. EDR detects all types of activity and gives it to your threat hunters so they can look for anomalies and respond to incidents. Responses to threats can also be automated. As a simple example, if a system detects a certain activity, it can trigger an automatic response to reboot. Something else to keep in mind is that EDR is a huge responsibility for an organization. You need to have dedicated individuals that continually look for malicious or mal-intending activities, make sense of those activities, and then trigger a response, whether it be automated or manual. There are companies that you can outsource to that are dedicated to the response category of, you can hire responders directly through Microsoft, or hire your own people and build your own security operation center to threat hunt and respond.
Automated Investigation and Remediation
This utilizes a lot of the same tools and processes that security analysts use and when there is a breach or an incident. Instead of assigning a resource, automated investigations can occur. This means that the system tries to put together linked events and looks for correlations so that you can try and determine causation. Finding all these different related activities allows you to start to piece together what’s going on, and determine if the threat is real/malicious, and if it is something you need to take further action on.
Automated investigation can be set up over time to do more and more automation with your input. You need to teach it how to be automated. For example, if you’re trying to detect a certain file you must tell it what file you’re looking for, or if you’re looking for an action to be created based on an alert, you must tell it which alert you’re looking for. The investigation is usually then manually started by your security team. You can also add notes about the incident, and then later automate if you choose to.
Access to Microsoft Threat Experts
When you’re in your console and threat hunting, you may find that it’s overwhelming or too much to take on due to the volume of threats facing your organization. Microsoft offers access to their threat experts as an outsourced service. This managed threat hunting service runs with Defender for Endpoint and gives you peace of mind knowing that you don’t have to watch all the activity. Microsoft will monitor for you and notify you when there’s something to be concerned about so you don’t have to look for the ‘needle in the haystack’. In conjunction with working with these threat experts, you will also need to work with experts on demand, with a partner like Finchloom, or with your internal security team to determine how to respond if something is detected. This is a feature that costs extra, but you have access to it with Defender for Endpoint P2.
Microsoft 365 Defender
With Microsoft 365 Defender, Defender for Endpoint and various Microsoft security solutions form a unified pre- and post-breach enterprise defense suite that natively integrates across endpoint, identity, email, and applications to detect, prevent, investigate, and automatically respond to sophisticated attacks.
In Summary
Defender P2 is the maximum security you can get from Microsoft when it comes to endpoint, and it costs a little bit more than P1, but you get access to so much more. It is important to remember that because of the extra features, you need to be conscious of who’s going to look after them. This is a big decision point, it’s not about spending the extra $2 to $3 per machine to get these features, it’s who is going to look at all this data, make sense of it, and respond to it.
Finchloom can walk your business through all the features of Defender for Endpoint P1 and P2 and determine which plan is right for you. If you are interested in a free consultation, please visit this page and fill out the form. To register for our Webinar for Defender P2 on March 10th at 11AM PST, please click here!
